Summary
- Cloud retention is convenient, but tin autumn unfortunate to information breaches. Use unreality retention with end-to-end encryption to support your files from leaking.
- Secure your credentials successful a password manager that encrypts passwords stored successful the cloud.
- Encrypt files shared online successful password-protected archives and region identifying accusation from shared documents.
It's practically intolerable to debar uploading files to the unreality these days: adjacent if you debar unreality sync tools similar OneDrive, you're yet going to request to stock thing with someone. Here are immoderate tips to trim the hazard of that information being utilized for unintended purposes.
Why You Need To Secure Your Cloud Uploads
"The cloud" has go a catch-all word for immoderate online storage—and it's ne'er been arsenic unafraid arsenic we'd similar to believe.
Online sync tools similar OneDrive, Dropbox, and iCloud store your files successful far-away information centers and tin revoke entree astatine immoderate time. Cloud email hosts store your emails and attachments connected servers that are extracurricular your control. Social media platforms alteration their privateness settings astatine the driblet of a hat, exposing accusation that was erstwhile private. Online record sharing, representation hosting, and different services are routinely breached, leaking earthy information that tin beryllium utilized to place you.
Once you've uploaded information into the cloud, it's perchance determination forever, adjacent if it looks similar you've deleted it. It could beryllium successful aged backups that haven't yet been purged by the provider, oregon simply marked arsenic deleted, but retained for continued usage per immoderate buried clause successful the company's privateness policy.
Given the modern necessity to stock files and accusation online, your lone existent enactment is to instrumentality measures to unafraid it and trim the hazard it poses if it is leaked.
Use Cloud Storage With Built-In End-To-End Encryption
If you're utilizing unreality synchronization tools to store files, take ones with end-to-end encryption. This means that the files are encrypted and decrypted connected your devices, utilizing a password that isn't stored successful the cloud, meaning the work supplier can't work it.
The astir fashionable end-to-end encrypted record synchronization instrumentality is Apple's iCloud, but it's constricted to Apple devices. Proton and NordLocker supply cross-platform solutions that enactment connected astir devices. If you trust connected unreality retention to store important files, you should marque definite you support your ain section copies arsenic well, conscionable successful lawsuit you suffer access, oregon idiosyncratic compromises your relationship and deletes them.

Proton Drive Review: It Could Be So Much More
A unafraid unreality retention work that misses the mark.
Secure Your Credentials successful a Password Database
In summation to helping you retrieve each the unique, strong passwords you're utilizing for each website and app (...right?), password managers encrypt each the info they store, truthful that their database files tin beryllium safely synced utilizing unreality tools.

Bitwarden
The champion escaped password manager is besides 1 of the champion password managers retired determination with its minimalist and straightforward interface. It's besides open-source, and adjacent the premium mentation is simply a bargain astatine lone $10 per year.
If your password manager database leaks, its contents cannot beryllium work without the encryption key, giving you a caput commencement connected changing your passwords and locking everything down. Many password-management apps volition besides automatically wide your clipboard aft you've copied and pasted a password from them, preventing the dreaded "pasted my password into chat alternatively of linking to a feline GIF" concern that has nary uncertainty led to a fewer compromised online accounts.
If you're utilizing a unreality file-sharing work to nonstop a record that's excessively ample for email, compress it into an encrypted ZIP archive, and stock the password with the recipient truthful lone they tin work it.
This prevents snooping by the sharing services themselves, oregon by anyone who manages to breach it oregon gets clasp of the download nexus for the file. This is peculiarly utile if sharing question oregon concern documents that incorporate delicate information.
Protect Your Cloud-Hosted Backups
If you indispensable usage online retention that isn't end-to-end encrypted to store backups (hey, it's usually free!), see storing immoderate delicate files successful an encrypted VeraCrypt container.
You tin safely store these containers online, and equine them erstwhile you request to adhd files to them, oregon retrieve data. Just remember, if you suffer your encryption key, thing you've secured with it volition beryllium everlastingly unreadable.
Redact and Watermark
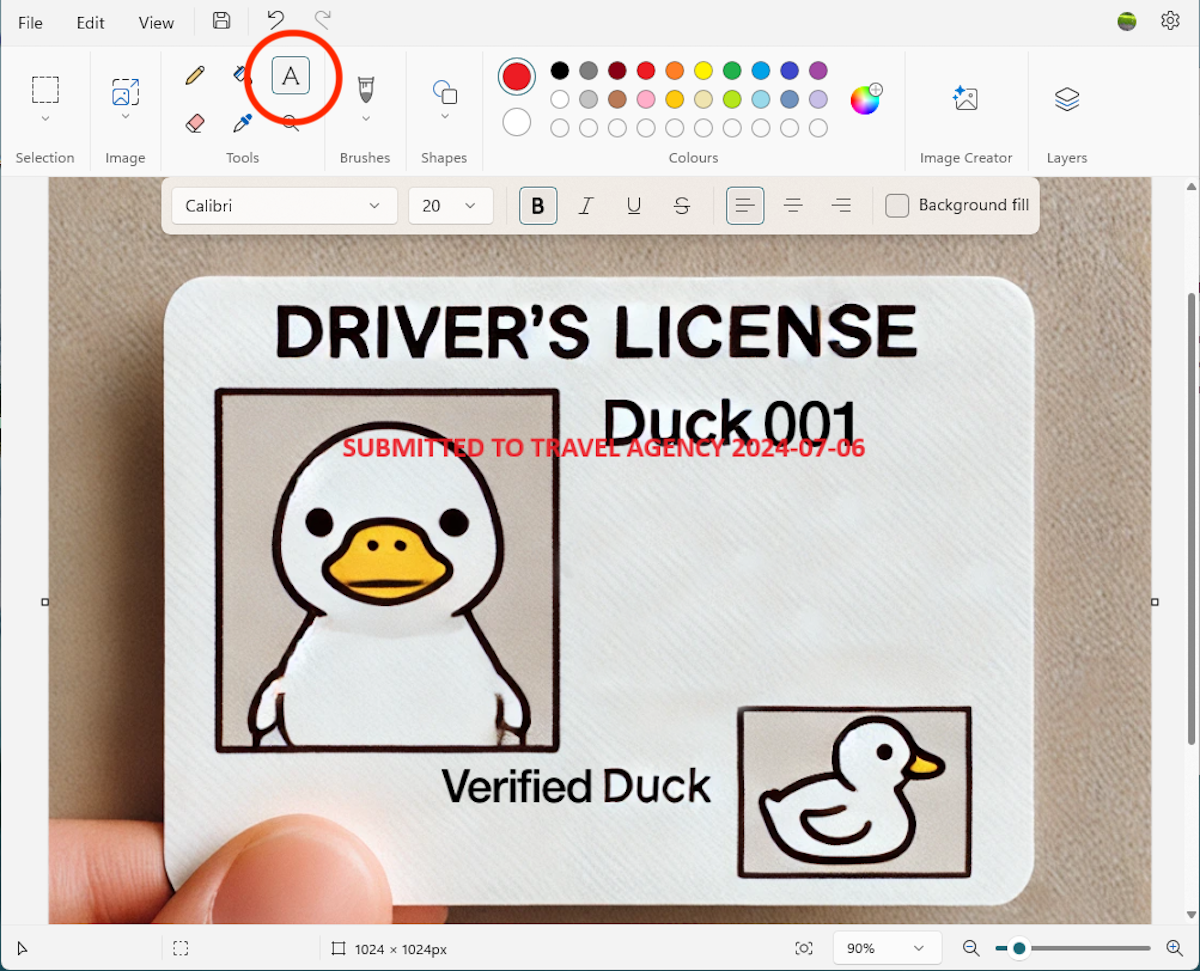
Remove EXIF information from photos earlier sharing them, truthful that they cannot beryllium utilized to find your location. You tin besides redact information to trim the harm successful a record leaking, oregon way wherever the leak came from: for example, if sharing slope statements for a rent application, marque definite your relationship numbers are blacked out.
You tin besides watermark documents by partially covering immoderate photos, truthful that they are harder to usage to impersonate you.
Cloud record sync and sharing services are ace convenient, but similar immoderate convenience, it comes astatine a cost. If you're acrophobic astir privacy, oregon conscionable don't privation to manus your info implicit to large tech, you tin inactive debar a batch of unreality platforms by hosting your ain services and utilizing peer-to-peer sharing services.
Syncthing tin regenerate unreality record sync tools, syncing your files straight betwixt your Windows, MacOS, and Linux devices without relying connected an intermediary. NextCloud tin beryllium installed connected a location server to physique your ain record sync work that you afloat control, and you tin besides usage Docker to big a assortment of apps similar online bureau suites and record transportation tools, each portion retaining implicit power of them.
All of this tin beryllium remotely accessed utilizing an easy-to-configure VPN similar TailScale. If you request immoderate hardware to big each of this connected and don't person a spare PC astir to commencement your homelab, you should see picking up a NAS. If this each sounds similar a spot of a project—it is, and it's ace rewarding erstwhile you get it each up and running.
.png)
 1 month ago
9
1 month ago
9








 English (US) ·
English (US) ·