Browser extensions tin beryllium a large mode to boost your productivity portion browsing. Chrome, which is the astir fashionable browser retired there, supports a wide scope of extensions, and truthful bash different Chromium-based browsers. However, these extensions are not ever beneficial. While galore are adjuvant for blocking ads, uncovering the champion deals oregon checking grammar errors, immoderate tin extremity up doing much harm than good.
I recently reported connected a radical of malicious extensions that were stealing idiosyncratic data, and present a caller study has flagged 35 much suspicious ones. These browser extensions petition unnecessary permissions and person been reported to cod and stock everything you bash online.
Join the FREE "CyberGuy Report": Get my adept tech tips, captious information alerts and exclusive deals, positive instant entree to my free "Ultimate Scam Survival Guide" erstwhile you motion up!

A antheral utilizing Google Chrome browser connected his laptop. (Kurt "CyberGuy" Knutsson)
Sketchy extensions successful the wild
A recent investigation by John Tuckner, laminitis of Secure Annex, revealed concerns astir 35 Chrome extensions, posing imaginable privateness and information risks. These extensions, galore unlisted connected the Chrome Web Store, were collectively installed implicit 4 cardinal times.
Many of these sketchy extensions presented themselves arsenic tools for hunt assistance, ad-blocking, information monitoring oregon hold scanning but shared a transportation to a single, unused domain, suggesting coordinated behavior. They each usage the aforesaid codification patterns, link to immoderate of the aforesaid servers and necessitate the aforesaid database of delicate systems permissions, including the quality to interact with web postulation connected each URLs visited, entree cookies, negociate browser tabs and execute scripts.
What’s much concerning is that astatine slightest 10 of these extensions carried Google’s "Featured" badge, implying vetting for trustworthiness. This raises questions astir Google’s reappraisal process, arsenic the badge suggests compliance with precocious standards for idiosyncratic experience, privateness and security.

A hacker astatine work. (Kurt "CyberGuy" Knutsson)
HOW TO STAY INCOGNITO AND CONCEAL YOUR NUMBER WHEN CALLING SOMEONE
Why are these extensions bad?
The main interest is the level of entree these extensions softly petition and however they usage it. With permissions to work tabs, entree cookies, intercept web requests and inject scripts into pages, they tin show astir everything you bash successful your browser. This includes tracking your browsing activity, observing login sessions and altering the contented of websites you visit, each without your knowledge.
These extensions are not simply misconfigured tools. They look to beryllium intentionally designed with surveillance successful mind. Many store their configuration information locally, which allows distant servers to update their behaviour astatine immoderate time. This setup is commonly seen successful spyware, wherever changes tin beryllium made aft installation without alerting the user. The codification is heavy obfuscated, making it hard for researchers to recognize what the extensions are really doing.
In immoderate cases, the extensions look to bash thing astatine each erstwhile clicked. However, they proceed to nonstop information successful the background. For instance, the Fire Shield Extension Protection remained inactive until the researcher manually triggered it with a circumstantial hold ID. Only past did it statesman to transmit browsing enactment and different data, revealing behaviour that would beryllium hard for an mean idiosyncratic to detect.

A idiosyncratic moving connected their laptop. (Kurt "CyberGuy" Knutsson)
MALWARE EXPOSES 3.9 BILLION PASSWORDS IN HUGE CYBERSECURITY THREAT
The 35 extensions to delete close now
The 35 extensions are not publically searchable connected the Chrome Web Store, meaning they tin lone beryllium installed via nonstop URLs. The afloat database of extensions is:
- Choose Your Chrome Tools
- Fire Shield Chrome Safety
- Safe Search for Chrome
- Fire Shield Extension Protection
- Browser Checkup for Chrome by Doctor
- Protecto for Chrome
- Unbiased Search by Protecto
- Securify Your Browser
- Web Privacy Assistant
- Securify Kid Protection
- Bing Search by Securify
- Browse Securely for Chrome
- Better Browse by SecurySearch
- Check My Permissions for Chrome
- Website Safety for Chrome
- MultiSearch for Chrome
- Global hunt for Chrome
- Map Search for Chrome
- Watch Tower Overview
- Incognito Shield for Chrome
- In Site Search for Chrome
- Privacy Guard for Chrome
- Yahoo Search by Ghost
- Private Search for Chrome
- Total Safety for Chrome
- Data Shield for Chrome
- Browser WatchDog for Chrome
- Incognito Search for Chrome
- Web Results for Chrome
- Cuponomia - Coupon and Cashback
- Securify for Chrome
- Securify Advanced Web Protection
- News Search for Chrome
- SecuryBrowse for Chrome
- Browse Securely for Chrome
How to region an hold from Google Chrome connected desktop
If you person installed 1 of the above-mentioned extensions connected your browser, region it arsenic soon arsenic possible. To region an hold from Google Chrome connected a desktop, travel these steps:
- Open Chrome and click the icon that looks similar a portion of a puzzle. You’ll find it successful the top-right country of the browser
- You tin spot each the progressive extensions now. Click the three-dots icon adjacent to the hold you privation to region and select Remove from Chrome
- Click Remove to confirm
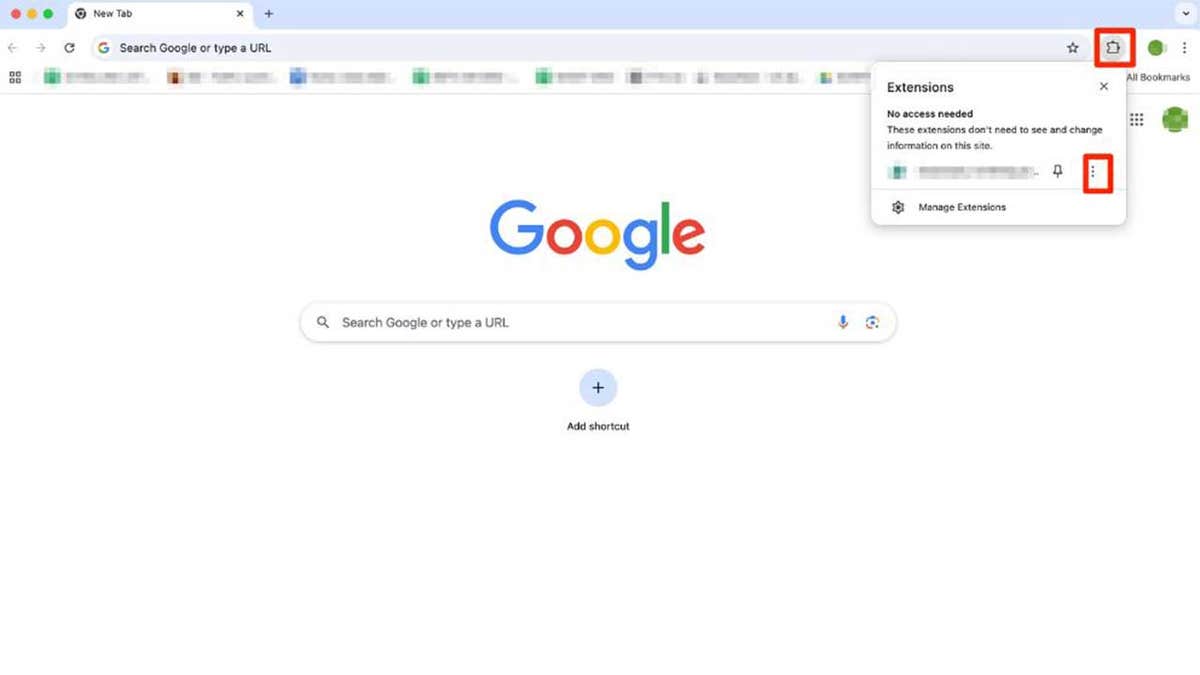
Steps to region an hold from Google Chrome. (Kurt "CyberGuy" Knutsson)
HOW TO REMOVE YOUR PRIVATE DATA FROM THE INTERNET
5 ways to enactment harmless from sketchy extensions
If you’re disquieted astir the supra extensions, present are 5 ways to safeguard your delicate accusation and support your online privacy.
1) Keep your browser up to date: Chrome gets regular updates that get escaped of astir information issues. Make definite you crook connected automatic updates for your browser (e.g., Chrome, Firefox, Edge) truthful you’re ever moving the latest mentation without reasoning astir it. See my usher on keeping your devices and apps updated for much information.
2) Install extensions lone from trusted sources: Official browser stores similar the Chrome Web Store person rules and scans to drawback atrocious actors. They’re not perfect, but they are inactive a amended enactment erstwhile compared to a random website connected the internet. Extensions from chartless websites oregon third-party downloads are acold much apt to fell malware oregon spyware.
3) Have beardown antivirus software: A bully antivirus tin pass you earlier you instal malicious software, specified arsenic sketchy browser extensions. It tin besides alert you to phishing emails and ransomware scams, helping support your idiosyncratic accusation and integer assets safe. Get my picks of the champion 2025 antivirus extortion winners for your Windows, Mac, Android and iOS devices.
4) Be skeptical of extensions requesting unnecessary access: Some extensions overreach connected purpose. A calculator instrumentality asking for your browsing past oregon a upwind app wanting your login information is simply a immense reddish flag.
Before installing, ask, "Does this support lucifer the extension’s job?" If the answer’s no, don’t instal it. Watch retired for wide permissions similar "Read and alteration each your information connected websites you visit" unless it’s intelligibly justified (e.g., a password manager). If an update abruptly adds caller support requests, excavation into why. It mightiness mean the hold has been sold oregon hacked.
5) Change your passwords and bash it safely: If you’ve ever saved passwords successful your browser (e.g., via Chrome’s built-in password manager oregon the "Save Password" prompt), those credentials could beryllium astatine hazard if a malicious hold was installed. These built-in managers store passwords locally oregon successful your Google, Microsoft oregon Firefox account, and a compromised browser tin springiness atrocious actors a mode in.
This doesn’t typically use to dedicated password manager extensions, which encrypt your information independently and don’t trust connected browser storage. However, if you're unsure whether an hold has been compromised, it's ever astute to update your maestro password and alteration two-factor authentication.
For maximum safety, alteration your astir important passwords (email, bank, shopping, unreality services) from a different, unafraid device, specified arsenic your telephone oregon different computer, wherever the questionable hold was ne'er installed. Avoid utilizing the aforesaid browser that whitethorn person been exposed. Then see switching to a password manager to make and store strong, unsocial logins going forward. I’ve reviewed the apical options successful my best password managers of 2025 guide. See which 1 fits your needs best.
Kurt’s cardinal takeaway
The information that respective of these extensions carried Google’s ain "Featured" badge should service arsenic a wake-up call. It points to a superior lapse successful oversight and raises concerns astir however thorough Chrome’s hold reappraisal process really is. When millions of users unknowingly instal spyware nether the content that it has been vetted and approved, the contented is nary longer conscionable astir atrocious actors. It reflects a deeper nonaccomplishment wrong the level itself. Google needs to instrumentality stronger work by improving transparency and tightening its reappraisal standards.
Do you deliberation browser makers similar Google should beryllium held much accountable for what gets published successful their stores? Let america cognize by penning america at Cyberguy.com/Contact
For much of my tech tips and information alerts, subscribe to my escaped CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter
Ask Kurt a question oregon fto america cognize what stories you'd similar america to cover.
Follow Kurt connected his societal channels:
Answers to the most-asked CyberGuy questions:
- What is the champion mode to support your Mac, Windows, iPhone and Android devices from getting hacked?
- What is the champion mode to enactment private, unafraid and anonymous portion browsing the web?
- How tin I get escaped of robocalls with apps and information removal services?
- How bash I region my backstage information from the internet?
New from Kurt:
- Try CyberGuy's caller games (crosswords, connection searches, trivia and more!)
- CyberGuy's exclusive coupons and deals
- Best gifts for Mom 2025
Copyright 2025 CyberGuy.com. All rights reserved.
Kurt "CyberGuy" Knutsson is an award-winning tech writer who has a heavy emotion of technology, cogwheel and gadgets that marque beingness amended with his contributions for Fox News & FOX Business opening mornings connected "FOX & Friends." Got a tech question? Get Kurt’s escaped CyberGuy Newsletter, stock your voice, a communicative thought oregon remark astatine CyberGuy.com.
.png)







 English (US) ·
English (US) ·