Do you instal a batch of antithetic apps connected your Linux computer? Are you disquieted that 1 of these apps mightiness person a microorganism oregon malicious codification that steals your data? Well, present are 5 information practices I personally travel to support my Linux PC harmless from these threats.
Linux is simply a reasonably unafraid operating system, but it's not virus-free. This is particularly existent for idiosyncratic similar maine who installs and reviews antithetic apps and software. My information risks are higher arsenic I tin accidentally instal thing with sudo privileges that ends up compromising my system. Thankfully, with astir a decade's acquisition successful investigating caller software, I've developed a strategy to support my Linux PC ultra-secure and virus-free.
5 Monitor Your Network Activity
One of my biggest information concerns is my information being stolen from my system. As a tech writer, I perpetually instal antithetic apps and tools connected my PC, and I would hatred it if 1 of them had immoderate malicious inclinations and decided to telephone location delicate information from my system.
To support myself from these types of mishaps, I usage Portmaster by Safing. It's a free and open-source (FOSS) web enactment show and exertion firewall. I tin usage it to cheque which apps are presently accessing the internet, what servers they are connecting to, arsenic good arsenic however overmuch information they are uploading and downloading. I tin besides usage it to artifact an app from accessing the net altogether.
For example, instrumentality a elemental calculator app I mightiness person downloaded. Portmaster tin archer maine if it's connecting to the internet, which is strange! But astatine the aforesaid time, it tin besides archer maine if it's uploading data—which is concerning, versus downloading data—which is understandable, particularly for currency conversion tasks! So, portion a calculator app accessing the net is worrisome, Portmaster helps maine recognize what it's doing, and marque an informed determination alternatively of being paranoid.
Of course, you could simply usage the terminal to get network-level power implicit your apps, but Portmaster makes it easier done an elegant and modern graphical interface.
Now, isolated from Portmaster, I besides usage taskbar widgets to support an oculus connected wide web postulation each the time. I personally usage the KDE Plasma desktop situation and the Network Monitor widget. But if you're connected GNOME, you tin usage the Vitals GNOME extension and get the aforesaid functionality.
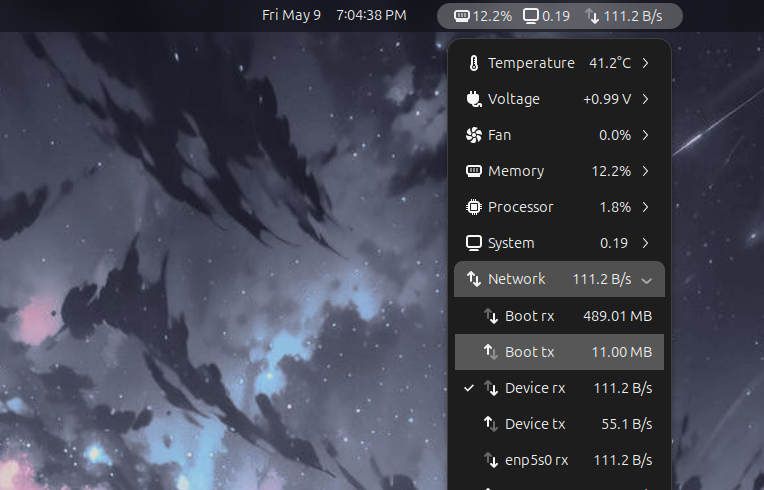
The thought present is to get a speedy presumption of the existent web traffic. I mostly person an thought of what mean web enactment looks like—download spikes during browsing, upload spikes during, well, uploading stuff. If I announcement important web enactment erstwhile I'm idle oregon conscionable typing successful a substance editor, I instantly cognize something's amiss and that it's clip to sojourn Portmaster to find retired what's wrong.
While a web show tin assistance you cheque if apps are stealing information from your system, it can't support you from installing a malicious app successful the archetypal place. This is wherefore I prioritize downloading apps from my distro's official repository (repo). These packages are vetted by the distro's maintainers and past made disposable to the you. As such, if you spot your distro, there's nary crushed to question the apps it's distributing.
That said, not each apps are ever disposable successful the authoritative repos. This is erstwhile I look into containerized options similar Flatpak. These apps tally successful a sandbox, making them mostly harmless to use, but don't spot them blindly. Some apps petition wide strategy access, which tin airs information risks. Therefore, ever cheque the permissions of an app earlier installing, spot if those are really indispensable for it, and then press the Install button. For Flatpaks, you tin mostly cheque the Flathub website to spot its information rating.
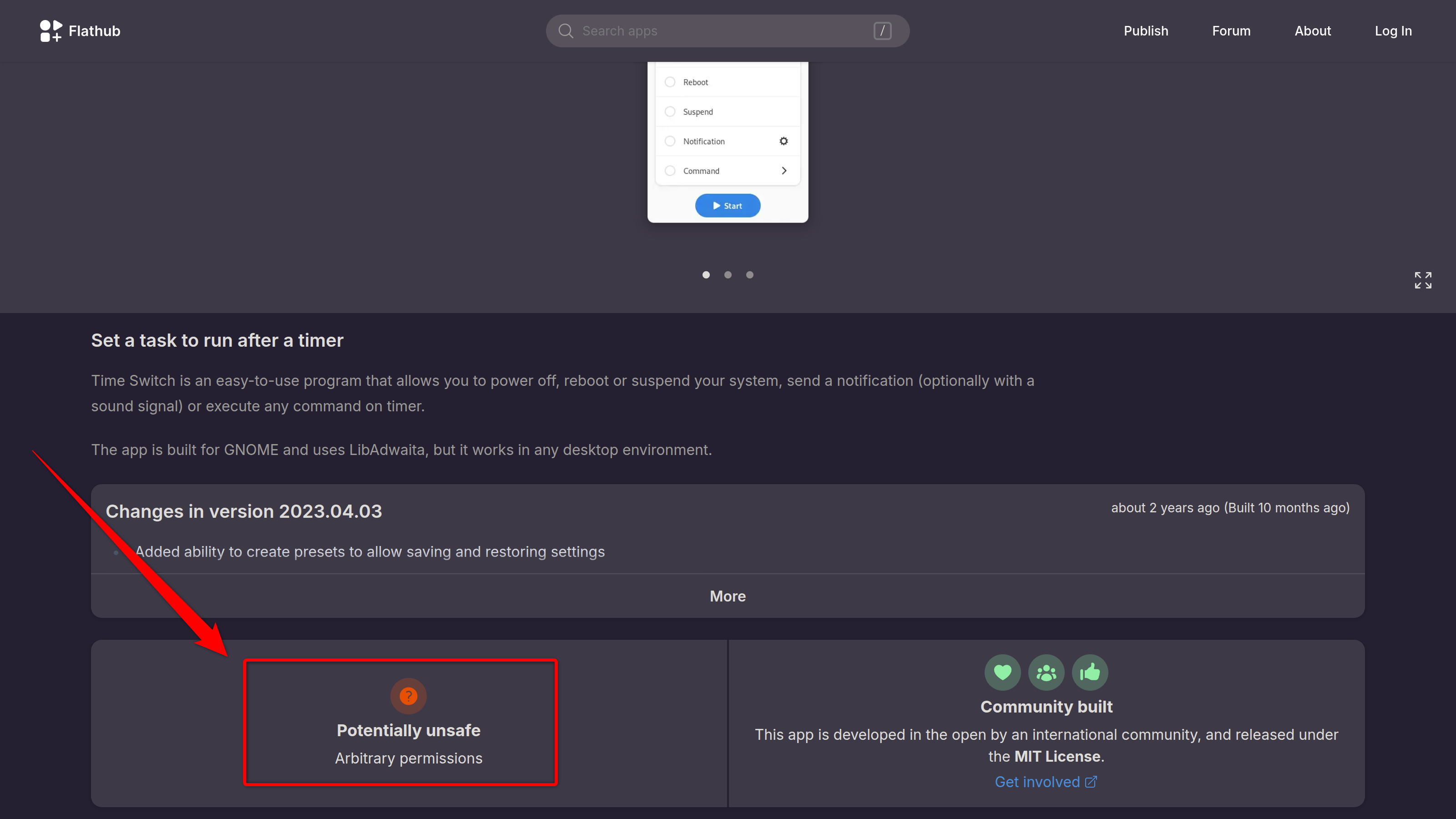
Sometimes I besides request to download worldly from third-party repos similar PPAs (Personal Package Archives) and the AUR (Arch User Repository). Here I travel a elemental regularisation of thumb: popularity equals scrutiny. If thousands of users instal an app from the AUR, there's a batch of eyes connected it to cheque for imaginable malicious code. That said, if you don't cognize astir the popularity of the app, you tin simply search for it connected Reddit, oregon your distro's authoritative forum and cheque what others person to say.
The tricky portion is erstwhile you request to instal immoderate random publication oregon tool, e.g., desktop widgets oregon customized themes from GitHub. This is wherever I cheque however galore radical are watching the task and however galore stars it has. Usually thing successful the thousands oregon precocious hundreds is capable to springiness maine confidence, arsenic astir of these radical are developers looking into the codification and not regular users.

Related
GitHub is the Best Place for Free and Open Source Software
GitHub contains astir each benignant of software, wholly for free. But navigating it is tough, truthful wherever bash you start?
If it's a tiny publication with a mates of 100 lines of code, you tin perchance bash a information audit yourself. You tin usage Gemini 2.5 Pro (known to beryllium bully astatine coding) to audit the app for you. Simply unfastened the GitHub leafage for the script, and successful the URL, alteration github to uithub. This volition amusement you the afloat repository operation and codification discourse which you tin present transcript and paste into Gemini 2.5 Pro and inquire it for an audit. For example, this URL:
https://github.com/vinceliuice/Mojave-gtk-themeBecomes:
https://uithub.com/vinceliuice/Mojave-gtk-themeAI and LLMs are inactive prone to making mistakes and hallucinating. As such, don't blindly spot what AI tells you astir the code. If it flags something, consult a nonrecreational astir it earlier deciding what to do.
3 Routinely Audit Installed Apps
Here's a trap I've fallen into before: assuming that once-secure bundle stays unafraid forever. I was a immense instrumentality of the Stacer strategy show app. It comes with a sleek and modern UI and provides broad strategy stats. However, until recently, I didn't cognize that the app was officially successful an abandoned authorities for the past 2 years.
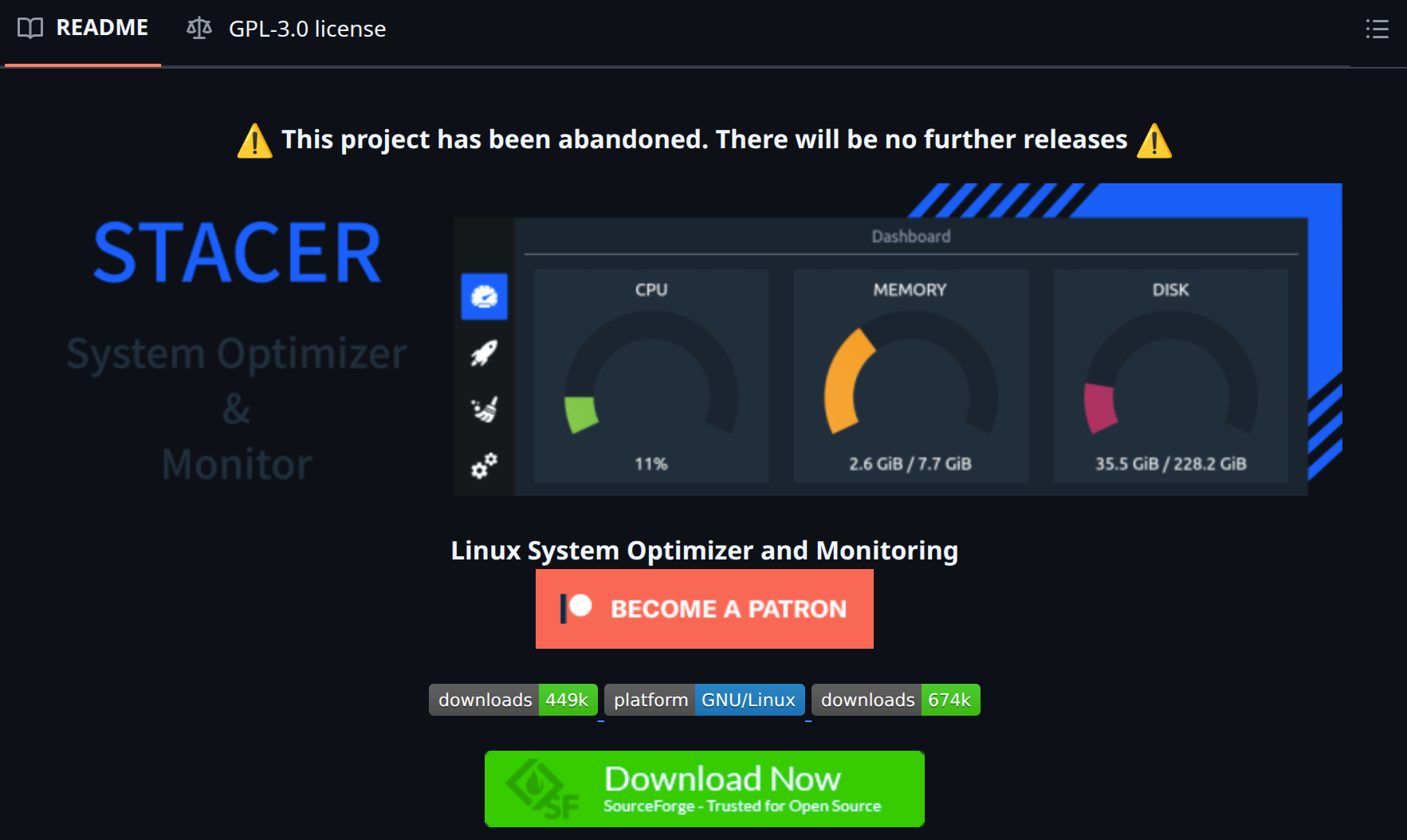
This matters due to the fact that abandoned bundle doesn't get information patches. If idiosyncratic discovers a vulnerability tomorrow, there's nary developer to hole it. I reluctantly removed Stacer from my strategy contempt it moving perfectly fine.
Now, if you don't privation to marque the aforesaid mistake that I did, see setting up Google Alerts for each azygous app you use. This way, whenever determination is immoderate quality astir those apps—whether it beryllium caller updates oregon information vulnerabilities—you'll cognize close away, and past you tin rapidly download the information spot the developers mightiness person issued oregon uninstall the app until they do.
This is wherefore astir information veterans promote keeping a fewer indispensable apps and uninstalling the ones you don't usage anymore. Each exertion expands your onslaught surface, and micromanaging everything tin go a immense chore.
Related
Why Are There So Many Zero-Day Security Holes?
Why bash these vulnerabilities support appearing? The reply is nuanced.
2 Enable 2FA for Your Desktop
This information instrumentality isn't wide known, but you tin really alteration two-factor authentication connected your Linux system, akin to however you unafraid your online accounts. I implemented this due to the fact that I person a applicable problem—the password I usage for my idiosyncratic relationship isn't peculiarly strong. Since I person to benignant it frequently, I usage memorable phrases alternatively than analyzable 64-character-long alphanumeric strings.
Now, by mounting up 2FA for my distro, I've added an other information furniture to compensate for my anemic password without making it intolerable to remember. This way, adjacent if idiosyncratic guesses my password, they inactive can't entree my strategy without the carnal instrumentality that generates my authentication codes.
That said, it tin beryllium somewhat inconvenient to participate a verification codification each clip you log successful oregon usage sudo successful the terminal, truthful I wouldn't urge this to everyone. In fact, astir of the information tips you effort to employment travel astatine immoderate outgo to your wide convenience, and I've personally decided I'm good with this.
1 Take Regular System Backups
While immoderate attacks purpose to bargain your data, others privation to destruct it oregon clasp it hostage done ransomware. Your champion defence against the second is simply a coagulated backup strategy. I support an automated backup system that regularly copies my indispensable files to the cloud. If you don't privation to prevention it successful the cloud, you tin besides prevention it to an outer thrust oregon a Network Attached Storage (NAS).

Related
How To Prepare For and Fight a Ransomware Attack
Ransomware is devastating, expensive, and connected the rise.
A cardinal constituent is not to support the backup of your strategy connected the strategy itself. This ensures that if my main strategy is compromised, my backups stay safe. I've seen excessively galore radical support their backups connected the aforesaid strategy they're backing up. This wholly misses the point—if your strategy is compromised oregon crashes, those backups spell down with it.
And determination you person it, the apical 5 things I bash to support my Linux PC harmless from viruses, hacks, and information threats. Feel escaped to replicate immoderate of these information measures into your ain workflow. That said, if you privation the implicit indispensable tips and tricks, cheque retired our beginner's usher to basal Ubuntu security.
.png)
 1 day ago
1
1 day ago
1









 English (US) ·
English (US) ·