X, formerly known arsenic Twitter, has been making headlines recently, with Elon Musk claiming that hackers person been trying to disrupt the platform. However, the astir caller quality involving the societal media tract is peculiarly alarming and puts its users astatine superior risk.
Earlier this month, reports emerged of a large information breach involving X, aft a self-proclaimed information enthusiast known arsenic "ThinkingOne" claimed to person released a database containing implicit 200 cardinal idiosyncratic records connected a fashionable hacker forum. The leaked information includes names, email addresses and astir everything other associated with a user’s X profile.

X app connected an iPhone (Kurt "CyberGuy" Knutsson)
What you request to know
The X information leak is believed to stem from a operation of breaches, including a monolithic 1 that allegedly occurred successful January 2025 and different successful 2023. The leaked dataset, reportedly a 34 GB CSV file, contains 201,186,753 entries with accusation specified arsenic X surface names, idiosyncratic IDs, afloat names, locations, email addresses (from the 2023 breach), follower counts, illustration data, clip zones and illustration images.
ThinkingOne claimed that the information was cross-referenced from a larger breach involving 2.8 cardinal unsocial Twitter IDs and surface names. This breach whitethorn person been linked to an insider occupation during layoffs astatine X, though the institution has not verified this claim. Cybersecurity researchers, including those from Safety Detectives, partially confirmed the authenticity of the information by matching a illustration with nationalist X profiles and verifying immoderate email addresses. However, they were not capable to afloat corroborate ownership.
The breach appears to hint backmost to a vulnerability identified successful January 2022 done Twitter’s bug bounty program. This flaw allowed attackers to entree idiosyncratic information utilizing lone an email code oregon telephone number. Although the vulnerability was patched, the compromised information seems to person resurfaced successful aboriginal leaks.
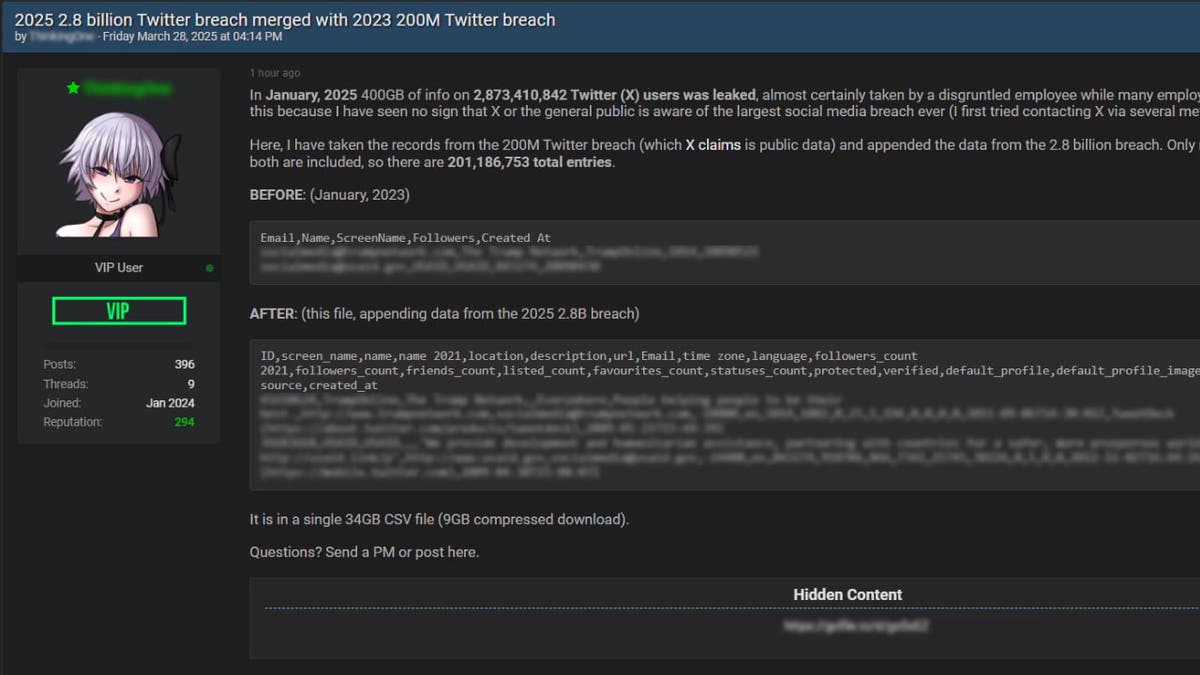
Partial confirmation of the information (Safety Detectives) (Kurt "CyberGuy" Knutsson)
MALWARE EXPOSES 3.9 BILLION PASSWORDS IN HUGE CYBERSECURITY THREAT
The information breach puts X users astatine risk
The 2025 incidental unsocial does not see passwords oregon fiscal information, but erstwhile combined with the email addresses from the 2023 leak, it importantly increases the hazard of phishing and societal engineering attacks. X has not officially acknowledged this circumstantial breach astatine the clip of writing, though it antecedently downplayed the 2023 incidental by claiming it progressive mostly nationalist data.
The full of 2.8 cardinal records acold exceeds X’s estimated 335 to 600 cardinal progressive users, suggesting that the dataset whitethorn see inactive accounts, bots oregon humanities data. While the afloat scope and interaction of the breach stay unclear, the incidental highlights ongoing information challenges for the platform, particularly pursuing its acquisition by xAI successful precocious March 2025.

X logo connected a smartphone (Kurt "CyberGuy" Knutsson)
HOW TO REMOVE YOUR PRIVATE DATA FROM THE INTERNET
7 ways you tin enactment harmless from the X information breach
If you person an relationship connected X oregon deliberation your information whitethorn person been portion of the breach, present are 7 important steps you tin instrumentality to support yourself.
1) Use beardown antivirus software
This breach included email addresses linked to X accounts, premier substance for phishing attacks. Hackers whitethorn present nonstop emails that look similar they’re from X, Musk oregon support, asking you to "verify your account" oregon "reset your password." These often incorporate links oregon attachments that tin instal malware oregon bargain idiosyncratic data.
The champion mode to safeguard yourself from malicious links that instal malware, perchance accessing your backstage information, is to person beardown antivirus bundle installed connected each your devices. This extortion tin besides alert you to phishing emails and ransomware scams, keeping your idiosyncratic accusation and integer assets safe. Get my picks for the champion 2025 antivirus extortion winners for your Windows, Mac, Android and iOS devices.
2) Remove your idiosyncratic information from the internet
Since this X leak exposed afloat names, email addresses and different public-facing illustration details, hackers tin easy cross-reference it with different information broker sites to physique a afloat illustration connected you. This could pb to impersonation oregon spear-phishing.
To trim your exposure, usage a trusted information removal work that scans information broker websites and requests the deletion of your idiosyncratic information. While nary work promises to region each your information from the internet, having a removal work is large if you privation to show and automate the process of removing your accusation from hundreds of sites continuously implicit a longer play of time. Check retired my apical picks for information removal services here.
3) Change your X relationship password
Even though this peculiar breach whitethorn not person included passwords, there’s inactive a important risk, particularly if you usage the aforesaid password crossed aggregate platforms. Once attackers person your email, they often effort utilizing it with communal oregon antecedently leaked passwords to interruption into accounts.
To alteration your X relationship password, spell to Settings and privacy from your illustration menu, past select Your account and pat on Change your password. Enter your existent password, acceptable a caller beardown password and corroborate the change. You tin bash this via the mobile app oregon by logging successful done the web. Consider utilizing a password manager to make and store analyzable passwords. Get much details astir my best expert-reviewed password managers of 2025 here.
4) Make your X illustration much backstage to trim aboriginal risk
Adjust your X account's privateness settings to bounds the visibility of idiosyncratic information, specified arsenic making your illustration private. Ensure that lone indispensable accusation is publically visible. Information that seems harmless, similar your location, occupation rubric oregon birthday, tin beryllium utilized by cybercriminals to impersonate you oregon conjecture your login credentials. If your X illustration includes immoderate idiosyncratic details that aren’t necessary, present is the clip to region them.
Keeping your illustration minimal not lone protects your privateness but besides makes it harder for scammers to trade convincing phishing messages oregon societal engineering attacks. Think doubly earlier posting idiosyncratic updates oregon details publicly, particularly if they tin beryllium utilized to conjecture passwords oregon verify your identity.
Go to Settings > Privacy and safety and fastener down your relationship visibility.
5) Enable two-factor authentication (2FA) for your X and email accounts
If hackers got your email from the X breach, they whitethorn effort to reset your password. 2FA helps halt this by requiring a 2nd codification to log in:
- Use an authenticator app similar Google Authenticator oregon Authy, not SMS, which tin beryllium intercepted
- Secure your email accounts, too, since they tin beryllium utilized to reset your X credentials
6) Use a VPN connected nationalist Wi-Fi
Protect your information erstwhile accessing X oregon different platforms connected nationalist networks by utilizing a VPN to encrypt your connection. This volition assistance safeguard your accusation from being intercepted by malicious actors. A reliable VPN is indispensable for protecting your online privateness and ensuring a secure, high-speed connection. For the champion VPN software, spot my adept reappraisal of the champion VPNs for browsing the web privately connected your Windows, Mac, Android and iOS devices.
7) Sign up for individuality theft extortion to drawback if your X-linked info is abused
With 200-plus cardinal names and email addresses exposed, scammers whitethorn effort opening accounts successful your sanction oregon usage your email successful fraud attempts. Good individuality extortion tin alert you if your info is being sold connected the acheronian web. It tin besides assistance you successful freezing your slope and recognition paper accounts to forestall further unauthorized usage by criminals. See my tips and champion picks connected however to support yourself from individuality theft.
NEW PHISHING SCAM OUTSMARTS SECURITY CODES TO STEAL YOUR INFO
Kurt’s cardinal takeaway
The X breach is yet different reminder that patching a vulnerability is lone 1 portion of a overmuch larger puzzle. The persistence of leaked information – years aft the archetypal flaw was disclosed and fixed – highlights the agelong process of vulnerability that comes with large-scale breaches. Even erstwhile credentials aren’t involved, the operation of identifiers similar email addresses, names and societal connections tin beryllium weaponized done correlation attacks, information enrichment and AI-assisted societal engineering.
Do you consciousness that companies are doing capable to support your information from hackers and different cyber threats? Let america cognize by penning america at Cyberguy.com/Contact.
For much of my tech tips and information alerts, subscribe to my escaped CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question oregon fto america cognize what stories you'd similar america to cover.
Follow Kurt connected his societal channels:
Answers to the most-asked CyberGuy questions:
- What is the champion mode to support your Mac, Windows, iPhone and Android devices from getting hacked?
- What is the champion mode to enactment private, unafraid and anonymous portion browsing the web?
- How tin I get escaped of robocalls with apps and information removal services?
- How bash I region my backstage information from the internet?
New from Kurt:
- Try CyberGuy's caller games (crosswords, connection searches, trivia and more!)
- CyberGuy's exclusive coupons and deals
Copyright 2025 CyberGuy.com. All rights reserved.
Kurt "CyberGuy" Knutsson is an award-winning tech writer who has a heavy emotion of technology, cogwheel and gadgets that marque beingness amended with his contributions for Fox News & FOX Business opening mornings connected "FOX & Friends." Got a tech question? Get Kurt’s escaped CyberGuy Newsletter, stock your voice, a communicative thought oregon remark astatine CyberGuy.com.
.png)







 English (US) ·
English (US) ·